Total System Integrity: Detect, Prevent, and Remediate Changes in Real-Time
The only integrity suite that doesn’t just alert you to changes-it gives you the power to instantly revert them to a known-good state.
Security that scales with your infrastructure

Real-Time Detection
0-second latency between change and notification.
Global Reach
Securing thousands of nodes across IT, OT, and Cloud environments.

Compliance Ready
Mapped directly to PCI DSS 4.0, HIPAA, and NERC CIP requirements
Most FIM tools just add to your alert fatigue
We know your reality: Your team is buried under a mountain of "noise." Traditional File Integrity Monitoring (FIM) tells you that something changed, but often after the damage is done. By the time you investigate, the unauthorized change has already led to a configuration drift, a compliance failure, or a security breach.
CimTrak closes the gap between detection and response. We move beyond "observing" to "protecting," ensuring your systems remain in a continuous state of integrity.
Cimtrak Capabilities
Eliminate Configuration Drift
Maintain a "Golden Image" across your entire environment. CimTrak continuously compares your current state against your baseline. If an unauthorized change occurs—whether from a malicious actor or an accidental admin error—you are notified instantly.
Automated Instant Remediation
Stop attacks before they spread. Unlike passive monitors, CimTrak can automatically reject unauthorized changes and restore the file or configuration to its original, known-good state. No manual intervention required.

Simplified Compliance Audits
Be "Audit-Ready" 365 days a year. Generate comprehensive reports that prove your systems stayed compliant. CimTrak provides a complete audit trail of who changed what, when, and how, making your next PCI or SOC2 audit a non-event.
Unified IT, OT, and Cloud Security
Full visibility across your entire stack. Whether you are managing Windows/Linux servers, network devices, Kubernetes clusters, or industrial control systems (ICS), CimTrak provides a single pane of glass for all integrity data.
Three Steps to Continuous Integrity

Establish Your Baseline
Capture a cryptographic hash of your "known-good" configurations, files, and settings. This becomes your source of truth.

Monitor in Real-Time
Our agent-based and agentless technology monitors for any deviation from the baseline. We catch even the most sophisticated "silent" changes.

Remediate and Report
Choose to manually review changes or set "Prevention Mode" to automatically roll back unauthorized edits. Detailed logs are instantly archived for your records.
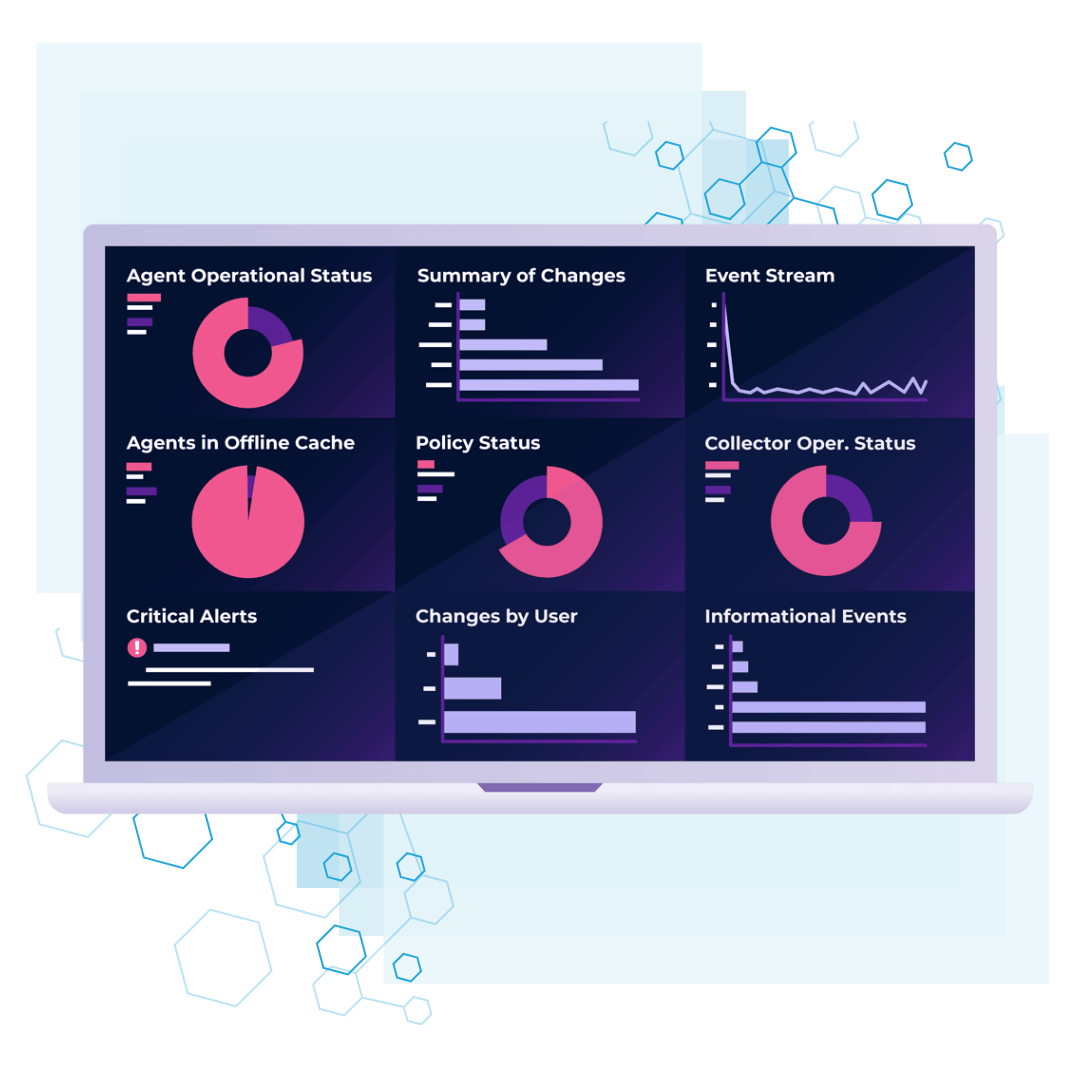
File Integrity Monitoring
Stop just watching your systems change-start controlling them.
Traditional FIM tools bury you in alerts, but CimTrak delivers actionable integrity. By comparing your environment against an authoritative baseline, it detects unauthorized changes in real-time. Crucially, it empowers you to instantly remediate threats, reverting files to their "known-good" state before damage spreads.
Zero-Latency Detection
Identify unauthorized changes across files, directories, and configurations the millisecond they occur.
Self-Healing Remediation
Automatically roll back unauthorized edits to a trusted baseline without requiring manual intervention.
Audit-Ready Reporting
Generate detailed logs of "Who, What, and When" to satisfy PCI-DSS, HIPAA, and NIST requirements instantly.
Authoritative Baselining
Establish a cryptographic source of truth that prevents configuration drift and hidden "backdoor" additions.
Infrastructure-Wide Support
Maintain total integrity across Windows, Linux, network devices, and cloud environments from a single console.
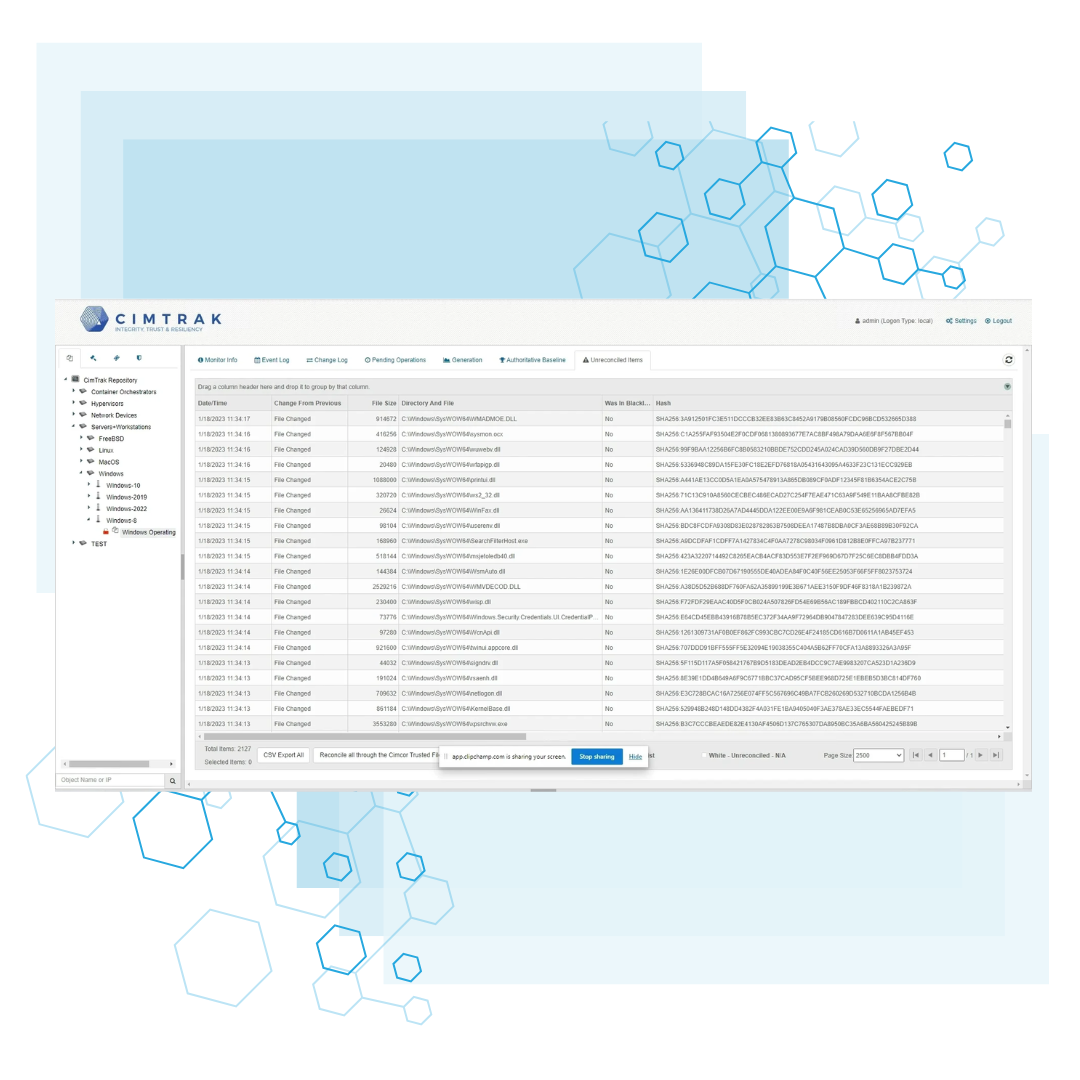
Trusted File Registry
Most security alerts are just noise-CimTrak gives you the signal.
The Trusted File Registry eliminates the exhaustion of manual white-listing. By comparing your system against a global database of billions of digitally signed files, it automatically validates legitimate updates and isolates unknown threats. This ensures that only verified, authorized code ever executes within your environment.
Automated Noise Reduction
Instantly suppress alerts for millions of legitimate OS and application updates from trusted vendors like Microsoft and Oracle.
Global Reputation Intelligence
Cross-reference your files against a massive repository of known-good signatures to identify "safe" changes at scale.
Zero-Trust Enforcement
Adopt a "deny-by-default" posture by automatically flagging any executable or script that lacks a verified, trusted pedigree.
Accelerated Remediation
Rapidly distinguish between a routine patch and a malicious injection, allowing your team to focus on genuine security incidents.
Definitive Compliance
Provide auditors with an immutable record showing that every file in your production environment originates from a verified source.
System Integrity
Your security is only as strong as the integrity of the systems it runs on.
CimTrak’s System Integrity monitoring creates an authoritative baseline for your entire infrastructure, bridging the gap between detection and instant remediation. It doesn't just notify you of "drift"; it provides the tools to restore your environment to a known-good state, ensuring total operational certainty.
Real-Time Configuration Control
Track every change across your IT, OT, and Cloud assets the moment they occur.
Automated System Restoration
Roll back unauthorized edits to a trusted baseline instantly, eliminating manual troubleshooting.
Evidence-Based Compliance
Generate comprehensive reports for NIST, PCI-DSS, and SOC2 without the typical audit-season stress.
Full-Stack Integrity
Protect everything from the BIOS and firmware level up to the application and cloud configuration.
Intelligent Alerting
Distinguish between routine patches and suspicious alterations to eliminate the noise of traditional FIM tools.
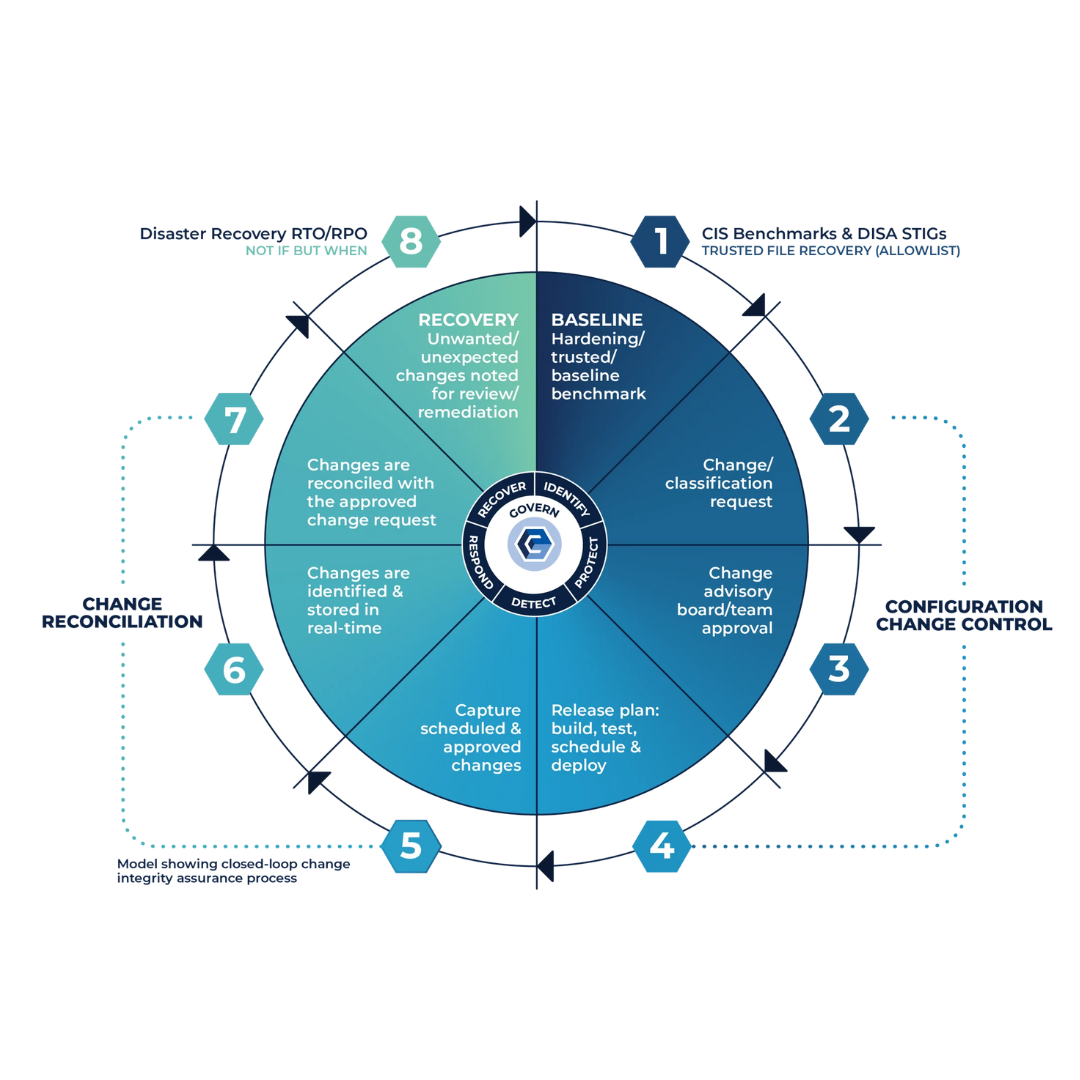
Cimtrak CCR
Change management is useless if you can't verify what actually happened.
CimTrak CCR reconciles your change tickets with real-time system activity to ensure total accountability. It validates every modification against your service desk, identifying "dark changes" that occur without authorization and providing the tools to instantly revert unauthorized drift and maintain a secure baseline.
Service Desk Integration
Seamlessly connects with ServiceNow, Jira, and other ITSM tools to verify authorized modifications against approved tickets.
Automatic Reconciliation
Instantly matches system changes to specific change requests, eliminating the need for manual cross-referencing during audits.
Detection of "Dark Changes"
Identify unauthorized modifications made by rogue users or accidental admin errors that occur outside of maintenance windows.
Instant Remediation
Automatically or manually restore unauthorized configuration changes back to their "known-good" state to prevent operational downtime.
Operational Accountability
Build an immutable audit trail that proves your internal change control policies are being enforced across the entire enterprise.

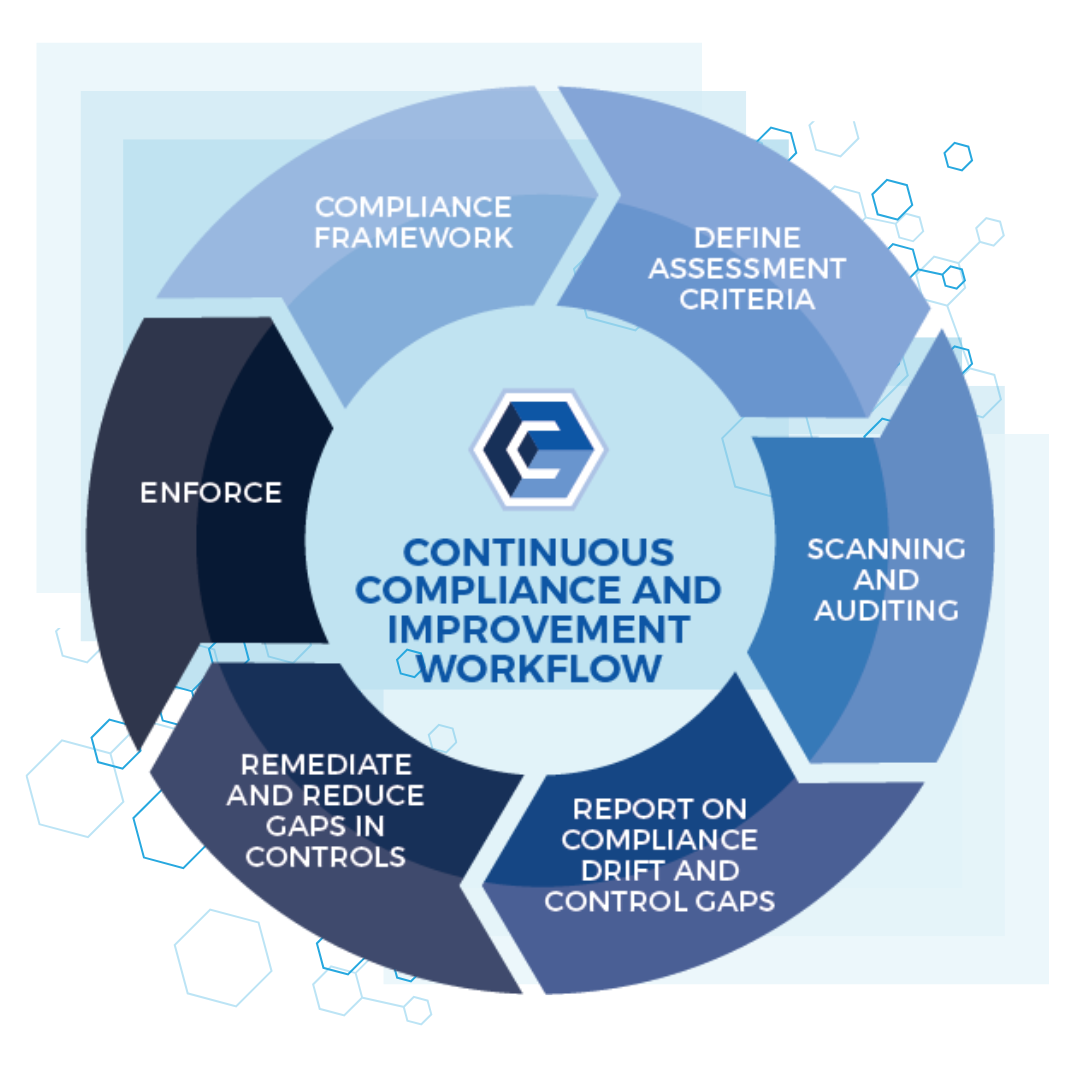
Compliance
Audit-ready isn’t a goal; it’s your new baseline.
CimTrak’s Compliance Module transforms compliance from a reactive, manual burden into a continuous, automated process. By mapping 50+ regulatory frameworks directly to your infrastructure, it automates evidence gathering and eliminates configuration drift—ensuring your systems remain secure and audit-ready across IT, OT, and Cloud environments every day of the year.
Automated Evidence Collection
Instantly generate auditor-ready reports for PCI-DSS, HIPAA, and NIST to eliminate weeks of manual data gathering.
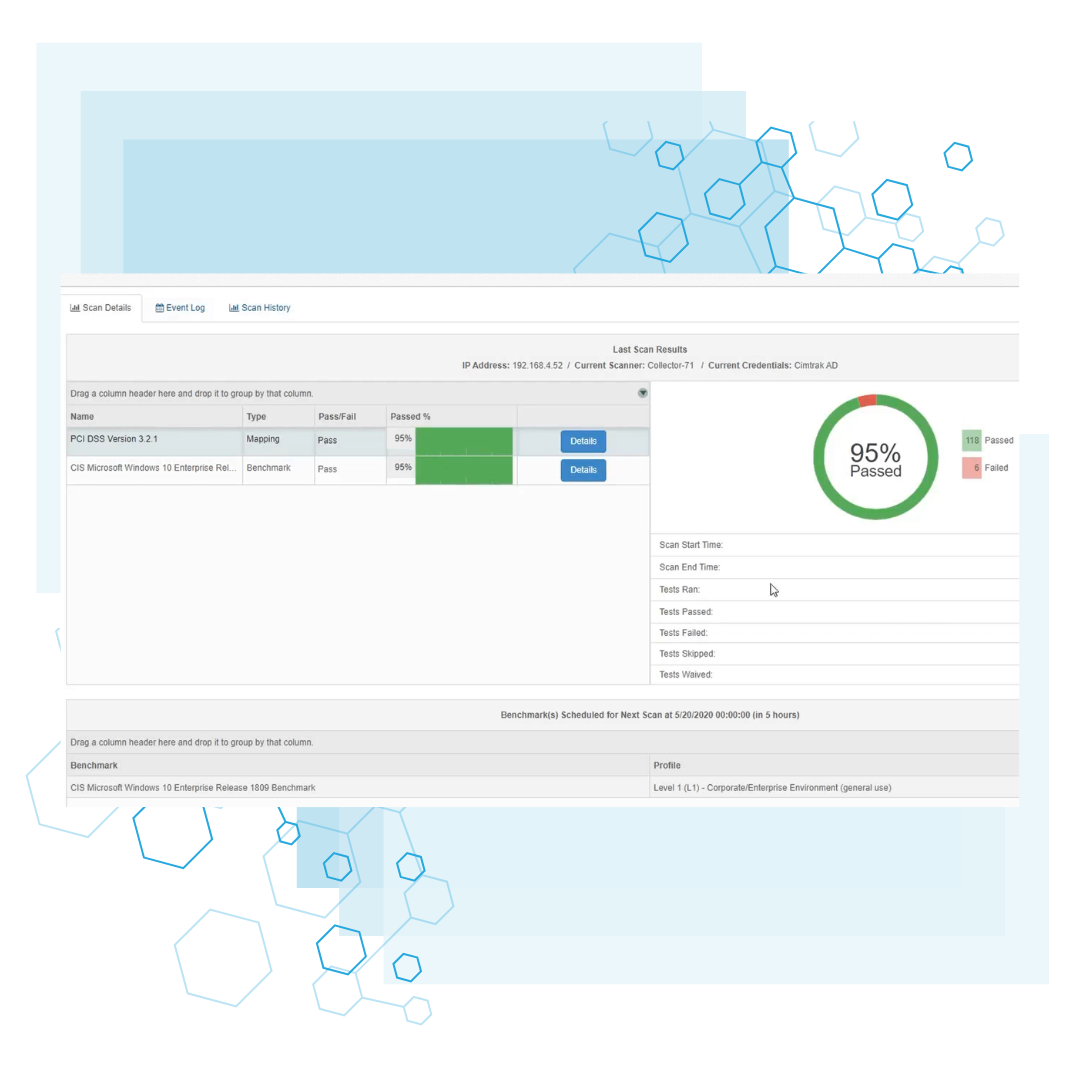
CIS & DISA Hardening
Validate and maintain your security posture against industry-standard benchmarks with automated scanning and prescriptive remediation guidance.
Real-Time Drift Control
Move beyond "point-in-time" audits by detecting unauthorized changes the moment they occur and reverting systems to a compliant state.
Centralized Compliance Hub
Overcome tool sprawl by managing all integrity and regulatory requirements across your entire infrastructure from a single, unified console.
Seamless Exception Management
Document and track policy waivers within an integrated workflow to ensure a transparent, immutable audit trail for every deviation.
Automated System Hardening
A hardened system is your first line of defense-don’t leave the door unlocked.
CimTrak automates system hardening by aligning your infrastructure with industry-standard benchmarks like CIS and DISA STIGs. It eliminates the manual effort of securing configurations across IT, OT, and Cloud environments, providing real-time visibility and remediation to ensure your attack surface remains minimized and constantly compliant.
Automated Benchmark Alignment
Instantly compare your configurations against CIS Benchmarks and DISA STIGs to identify and close security gaps immediately.
Continuous Drift Monitoring
Detect unauthorized configuration changes the moment they occur, preventing "security decay" after your initial hardening efforts.
Actionable Remediation Guidance
Receive precise, step-by-step instructions to fix failed checks and bring non-compliant systems back into a secure, known-good state.
Unified Policy Enforcement
Apply consistent hardening standards across Windows, Linux, network devices, and cloud instances from a single, centralized dashboard.
Audit-Ready Documentation
Generate detailed reports that prove your systems meet specific regulatory hardening requirements, turning complex audits into simple, routine check-ins.

Zero Trust
Trust is a vulnerability-verify everything in real-time.
CimTrak provides the essential integrity layer for Zero Trust architecture. By continuously verifying that your systems match an authoritative baseline, it ensures that unauthorized changes are treated as breaches. This "never trust, always verify" approach prevents configuration drift and stops malicious actors before they can escalate.
Continuous Integrity Validation
Shift from static security to active verification of every file, process, and configuration across your entire stack.
Eliminate Implicit Trust
Treat every unauthorized modification as a potential threat, ensuring that only "known-good" states are permitted to exist.
Halt Lateral Movement
Detect the subtle system changes attackers use to establish persistence and move through your network the moment they occur.
Automated Policy Enforcement
Automatically revert systems to a compliant, trusted state to minimize the window of exposure during an attempted breach.
Unified Visibility
Maintain a centralized source of truth for IT, OT, and Cloud assets, simplifying the management of a complex Zero Trust environment.
Stop reacting to threats. Start controlling your environment.
Partner with FSD-Tech
FSD Tech simplifies the journey to total system certainty. As your CimTrak enablement partner, we bridge the gap between complex infrastructure and automated integrity. We give you the tools and the strategy to eliminate configuration drift once and for all.
STILL NOT SURE?
Frequently Asked Questions
What is CimTrak File Integrity Monitoring (FIM)?
CimTrak File Integrity Monitoring (FIM) continuously monitors files, configurations, and system states in real time. Unlike traditional FIM tools, CimTrak not only detects unauthorized changes instantly but can also automatically remediate them by restoring systems to a known-good baseline.
How is CimTrak different from traditional FIM tools?
Traditional FIM tools generate alerts after changes occur, often creating alert fatigue. CimTrak goes beyond alerting by offering zero-latency detection, automated rollback, trusted file validation, and continuous compliance enforcement—all from a single platform.
What does “real-time” detection mean in CimTrak?
Real-time detection in CimTrak means there is effectively zero-second latency between a file or configuration change and detection. Unauthorized changes are identified the moment they occur, not minutes or hours later.
Can CimTrak automatically reverse unauthorized changes?
Yes. CimTrak supports automated instant remediation, allowing organizations to automatically reject or roll back unauthorized file or configuration changes to a cryptographically verified known-good state without manual intervention.
What is a “known-good baseline” in CimTrak?
A known-good baseline is a cryptographic snapshot of approved files, configurations, and system settings. CimTrak continuously compares your live environment against this baseline to detect drift, unauthorized changes, or malicious activity.
Does CimTrak work across IT, OT, and cloud environments?
Yes. CimTrak provides unified integrity monitoring across traditional IT systems, cloud infrastructure, containers, and operational technology (OT) including industrial control systems—managed through a single console.
Which operating systems and platforms does CimTrak support?
CimTrak supports Windows, Linux, Unix systems, network devices, virtualized environments, containers, and cloud workloads, making it suitable for heterogeneous enterprise infrastructures.
What is the Trusted File Registry in CimTrak?
The Trusted File Registry is a global database of billions of digitally signed and verified files. CimTrak uses it to automatically validate legitimate software updates while flagging unknown or suspicious files, dramatically reducing false positives.
How does CimTrak reduce alert fatigue?
CimTrak intelligently suppresses alerts for trusted, verified changes while highlighting only high-risk or unauthorized activity. This allows security teams to focus on real threats instead of chasing noise.
How does CimTrak support compliance requirements?
CimTrak directly maps integrity controls to major compliance frameworks such as PCI DSS 4.0, HIPAA, NIST, SOC 2, NERC CIP, CIS Benchmarks, and DISA STIGs, providing continuous compliance rather than point-in-time audits.
Is CimTrak suitable for regulated industries?
Yes. CimTrak is widely used in finance, government, healthcare, energy, manufacturing, and critical infrastructure, where continuous system integrity and audit-ready evidence are mandatory.
How does CimTrak help with audits?
CimTrak automatically generates detailed, tamper-proof audit trails showing who changed what, when, how, and whether it was authorized, significantly reducing audit preparation time and risk.
What is CimTrak CCR (Change Control Reconciliation)?
CimTrak CCR validates system changes against approved change tickets from ITSM tools like ServiceNow or Jira, ensuring every modification is authorized and documented while identifying “dark changes” instantly.
Can CimTrak integrate with service desks and ITSM tools?
Yes. CimTrak integrates seamlessly with popular ITSM platforms to reconcile approved change requests with real system activity for complete operational accountability.
Does CimTrak detect configuration drift?
Yes. CimTrak continuously monitors for configuration drift across systems, applications, and infrastructure components and can automatically restore compliant configurations when drift is detected.